Encryption Isn’t Enough Anymore
Once upon a time, encryption was the gold standard. Today? It’s just table stakes. While businesses rest on yesterday’s security protocols, fraudsters are already executing tomorrow’s heists. This is no longer a passive game of defense — it’s an invisible war. And right now, you’re either outsmarting cybercriminals or being quietly breached by them.
Payment security refers to the processes and technologies used to protect payment transactions, ensuring sensitive data is safeguarded and fraud is prevented in both online and offline systems.
Every business that accepts credit cards as a form of payment should have security measures in place for all financial transactions. Modern payment gateways and processors rely on advanced encryption protocols, such as Secure Sockets Layer (SSL), to establish secure communication channels and protect online payment data from cyber threats. But here’s the secret they don’t want you to discover: Corytech’s security stack isn’t just built to protect — it’s designed to dominate.
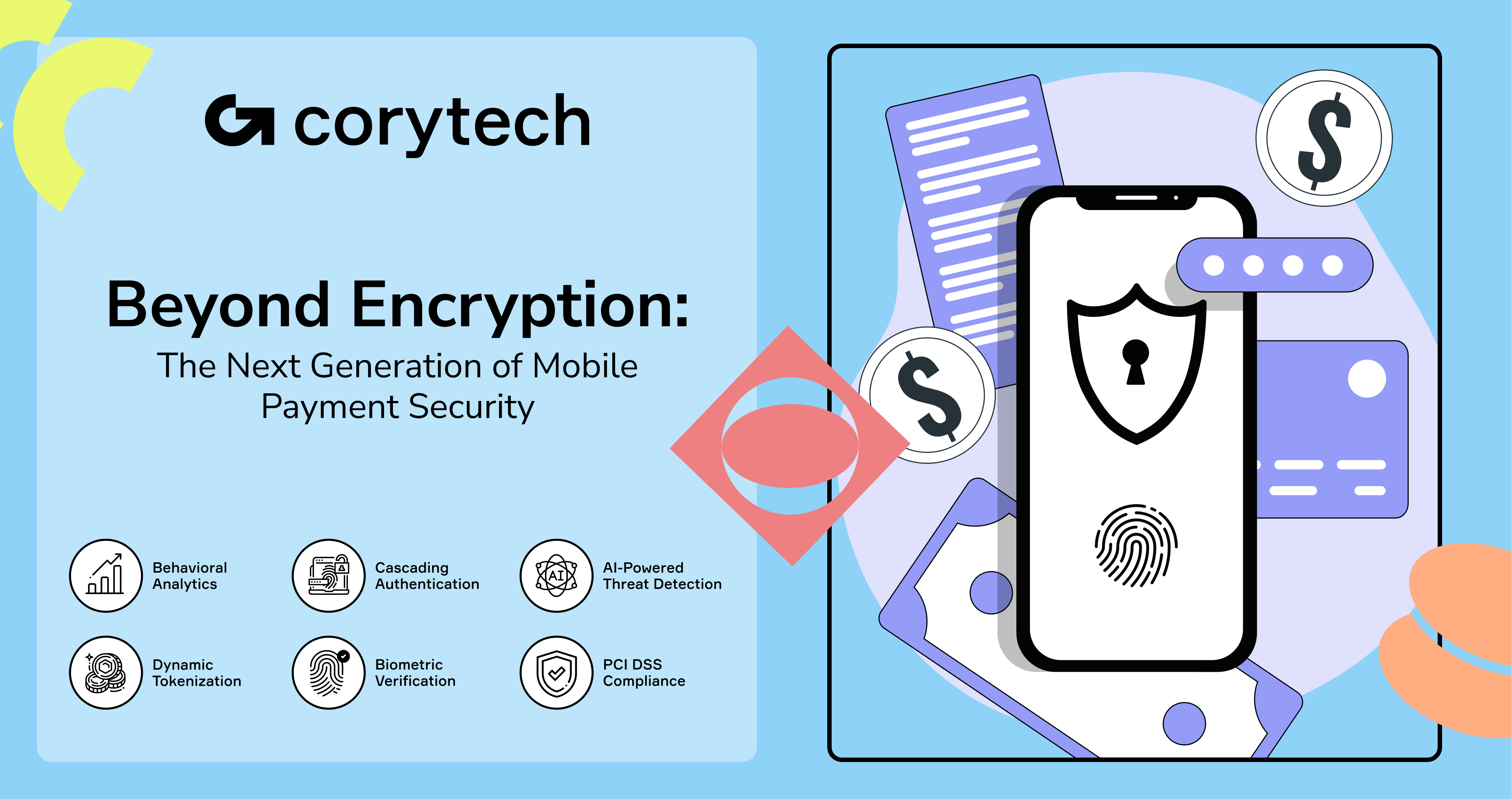
The Hidden Backbone: Payment Gateways and Processors Explained
When you make an online purchase, there’s a lot more happening behind the scenes than meets the eye. Payment gateways and processors are the unsung heroes of online payment security, working tirelessly to ensure every financial transaction is seamless and secure.
A payment gateway acts as the digital gatekeeper, encrypting sensitive customer data and authorizing each transaction in real time. Meanwhile, the payment processor is the engine that moves funds between your customer’s bank and your business’s account, making sure the money lands where it should. Both are essential for secure payments, but their true value lies in the security measures they enforce.
To protect against data breaches and fraudulent transactions, payment gateways and processors must adhere to strict PCI DSS compliance standards. This means robust encryption, tokenization, and two-factor authentication are not optional—they’re mandatory. Choosing a reputable payment gateway and processor that prioritizes payment security is one of the smartest moves a business can make.
By understanding how these systems work together to safeguard sensitive data, you’re not just facilitating online payments—you’re building a fortress around your customers’ trust.
Why Fraudsters Are Smarter Than You Think
And why traditional security tools are no longer enough
The belief that fraud can be stopped by a firewall and some password policies—such as a traditional network security firewall— is dangerously outdated. While a network security firewall has long played a key role in protecting business networks by creating a barrier between trusted internal networks and untrusted external networks, today’s fraudsters are organized, tech-savvy, and often funded like startups. They use AI to mimic human behavior, spin up synthetic identities that bypass KYC protocols, and launch multi-vector attacks that overwhelm traditional security systems. Relying solely on basic network security is no longer sufficient to protect sensitive customers data from modern threats and cyberattacks. Fraud prevention techniques include machine-learning algorithms that analyze transaction patterns, enabling businesses to detect and mitigate threats more effectively. In fact, 71% of businesses reported that they were targeted by payment fraud in 2021, highlighting the scale of the challenge.
Consider this:
- In 2024, iGaming platforms saw a 37% increase in attacks involving synthetic identities.
- 62% of PSPs reported losses due to session hijacking and bot-driven velocity attacks.
- Fraud-as-a-Service platforms now offer pre-built attack kits — complete with dashboards and customer support.
This isn’t petty crime — it’s a professional ecosystem, and your current defense might be leaving the doors wide open.
The New Payment Security Standard: Proactive, Not Reactive
From encryption to intelligence-driven defense
Security needs a paradigm shift. Encryption and tokenization are essential, but they don’t think. To truly stay ahead, you need intelligence that predicts and adapts in real-time. Tokenization replaces sensitive payment information with unique tokens that have no intrinsic value if compromised, adding an extra layer of security to payment systems. Both encryption and tokenization are used to secure payment information, ensuring sensitive data remains protected even in the face of evolving threats. Asymmetric encryption, which uses a public key to encrypt and a private key to decrypt sensitive payment data, provides a higher level of security for data transmissions. It is crucial to establish a secure connection using protocols like Transport Layer Security (TLS) to protect data in transit and safeguard against cyber threats.
Corytech’s approach integrates initiatives that are frequently highlighted in media about us coverage.
- Behavioral analytics that continuously learn and refine threat models.
- Adaptive risk assessment that evaluates transactions based on thousands of data points, not just binary checks.
- Real-time anomaly detection that stops unknown threats before they become known ones.
Being reactive puts you at the mercy of fraud. Being proactive flips the dynamic. Now you’re not just a harder target — you’re an impossible one.
Meet the Tribe: Businesses Who Refuse to Be Targets
Why leading PSPs and gaming platforms are joining a new security culture
There’s a new tribe forming — resilient, agile, and unbreakable. These are the businesses that don’t wait for a breach to take action. They integrate Corytech’s technology not just to protect data, but to protect their brand, their partners, and their players.
Members of this tribe use:
- Dynamic rule engines that evolve as threats evolve.
- Multi-layered tokenization that renders stolen data useless.
- Invisible authentication flows that add zero friction to legitimate users, and maximum resistance to fraudsters. These flows often incorporate biometric authentication and multi factor authentication to verify user identities. Biometric data, such as fingerprints or facial recognition, is increasingly used to enhance security in payment authentication.
They don’t ask if they’ll be attacked — they assume it. And they plan to win.
PCI DSS and the Compliance Conundrum: What You Need to Know
PCI DSS compliance isn’t just a checkbox—it’s the foundation of modern payment security. The Payment Card Industry Data Security Standard (PCI DSS) sets the rules for how businesses must protect cardholder data and defend against data breaches. If your business handles credit card transactions, these security standards are non-negotiable.
PCI DSS requirements demand a multi-layered approach: firewalls to block external threats, encryption to shield sensitive data, and strict access controls to ensure only authorized personnel can touch customer information. Regular risk assessments and timely security patches are essential to stay ahead of evolving threats.
Failing to comply isn’t just risky—it’s expensive. Non-compliance can lead to hefty fines, reputational damage, and a loss of customer trust. But by making PCI DSS compliance a core part of your payment security strategy, you’re not just protecting sensitive customer data—you’re demonstrating your commitment to secure transactions and industry best practices.
-(9).png)
Trusted Allies: Managing Payment Security with Partners
In today’s interconnected world, few businesses handle payment processing entirely in-house. Third-party vendors and partners are often part of the payment ecosystem, making it critical to manage payment security beyond your own walls.
The key? Choose partners who treat payment security as seriously as you do. Look for those with a robust payment security strategy—think encryption, tokenization, and two-factor authentication as standard, not extras. Ensure every partner is PCI DSS compliant and upholds the highest security standards for protecting sensitive customer data.
But don’t stop at onboarding. Regularly monitor your partners’ security practices and demand transparency. By working only with trusted allies who share your commitment to payment security, you strengthen your entire payment infrastructure and keep your customers’ sensitive data safe from external threats.
Inside Corytech's Anti-Fraud Arsenal
What the fraudsters don’t want you to know about
Corytech’s anti-fraud tools are designed to enhance payment security and ensure secure payments for all users. By leveraging advanced technology and industry best practices, Corytech sets a new standard for payment processing security in the industry.
What if you could see what fraudsters fear the most? Here’s a peek inside Corytech’s anti-fraud arsenal:
Behavioral Fingerprinting in Real Time
Corytech builds dynamic profiles for every user — tracking mouse movements, click velocity, scroll depth, and even typing rhythm. The moment something’s off, the system acts.
Velocity and Pattern Analysis
Rapid transactions, repeated login attempts, or strange timing? Corytech’s velocity checks catch high-speed fraud in its tracks.
Dynamic Tokenization Layers
Static tokens are dead. Corytech rotates tokens based on risk context — device, geo, session data — making it exponentially harder to reuse stolen credentials.
Cascading Authentication for Protecting Cardholder Data
Forget one-size-fits-all MFA. Corytech escalates authentication only when needed, preserving user experience while choking fraud attempts.
These are the tools fraudsters wish you didn’t have. But now you do.
Monitoring and Maintaining Payment Security: Staying Ahead of Threats
Payment security isn’t a one-and-done deal—it’s a continuous process. Staying ahead of security threats means constantly monitoring your systems, conducting regular risk assessments, and applying security updates and patches as soon as they’re available.
A robust payment security strategy should include advanced security measures like encryption, tokenization, and two-factor authentication to protect sensitive customer data at every stage of the payment process. Regular security audits and compliance checks help you spot vulnerabilities before hackers do, while staying informed about the latest trends in payment security ensures your defenses are always up to date.
By making payment security an ongoing priority, you not only protect your customers’ sensitive data but also reinforce their trust in your brand—no matter how the threat landscape evolves.
Us vs. Them: Turning the Tables on Threat Actors
The psychology of winning the fraud war
This isn’t just a technology race. It’s a mindset shift. For too long, businesses have played defense — patching holes, responding to breaches, and hoping compliance is enough. To truly protect your business, it’s crucial to assess your current payment infrastructure to identify vulnerabilities and areas for improvement. But Corytech empowers you to flip the script.
Corytech helps businesses address payment security challenges by implementing robust security measures and creating a secure environment for every transaction.
“Us vs. Them” isn’t fear-mongering. It’s clarity. You’re building trust with every transaction. Fraudsters are trying to dismantle that trust. Corytech’s tech ensures your side stays one step ahead.
- Real-time countermeasures.
- Network-wide threat intelligence sharing.
- Seamless orchestration across PSPs, gaming platforms, and financial institutions.
It’s not about surviving the next attack. It’s about owning the battlefield.
The Real Cost of Payment Security: Investment vs. Exposure
Let’s face it: investing in payment security isn’t cheap. But the alternative—a data breach—can be catastrophic. The average cost of a data breach now exceeds $4 million, not to mention the long-term damage to your reputation and customer trust.
Robust payment security measures, including encryption, tokenization, and two-factor authentication, are essential investments for any business that wants to protect sensitive customer data and prevent fraudulent transactions. While the upfront costs may seem high, they pale in comparison to the financial and reputational fallout of a security breach.
Think of payment security as insurance for your business’s future. By prioritizing these investments, you’re not just complying with industry standards—you’re safeguarding your customers, your revenue, and your brand from the devastating impact of exposure.
Why C-Level Leaders Are Leading the Security Charge
It’s not just IT’s problem anymore
The financial damage from a breach is obvious. But what about the brand erosion? The trust shattered? The boardroom fallout? The average cost of data breaches globally hit an all-time high of $4.45 million in 2023, underscoring the immense financial stakes involved.
Security is no longer just an IT metric — it’s a strategic priority. C-level leaders are stepping in because they understand what’s at stake:
- Reputation: One incident can destroy years of brand equity.
- Compliance: With evolving regulations like DSA, PSD3, and MiCA, inaction is costly, and ongoing compliance efforts are required to keep up with these changes.
- Investor Confidence: Stakeholders demand resilience, not excuses.
With Corytech, leadership can confidently say: We’re covered — from endpoint to ecosystem.
Join the Movement: Futureproof Your Platform
Simple, seamless integration with Corytech
You don’t need an overhaul. Corytech’s anti-fraud and payment orchestration layers are built for easy implementation and maximum interoperability. A secure payment gateway acts as an intermediary between the customer, business, and financial institutions involved in a transaction, ensuring seamless and protected payment processing.
Choosing reputable payment gateway providers and payment processors is crucial for maintaining security, reliability, and compliance with industry standards. While established providers like PayPal and Authorize.net may charge transaction fees, these costs are justified by the advanced security features and fraud protection they offer. Integrating Corytech helps protect your entire payment system from external threats and vulnerabilities. Key features of secure payment gateways include authentication, encryption, and tokenization of cardholder information throughout payment processing.
What you gain:
- Instant access to the latest fraud detection innovations.
- Modular integration that doesn’t disrupt operations.
- A community of secure, successful PSPs and gaming platforms.
Join the businesses who’ve decided enough is enough. Protect your community, your revenue, and your future.
The Security Revolution Against Data Breaches Has Already Started
Will you lead it or chase it?
Fraudsters evolve daily. So should your defenses. Corytech isn’t just offering tools — we’re building a future where fraud is outmatched at every turn. Regularly updating systems addresses known vulnerabilities and improves overall security, ensuring businesses stay ahead of emerging threats. Conducting a risk assessment helps businesses identify vulnerabilities in their payment infrastructure, enabling them to proactively address potential threats.
Protecting cardholder data and taking steps to protect customer data are essential to prevent breaches and maintain trust. It is crucial to secure credit card details, credit card data, and payment data throughout all payment processes to comply with industry standards and safeguard sensitive information. By implementing these best practices, businesses can ensure payment security for themselves and their customers.
You’ve seen what’s possible. You’ve seen what’s at stake. Now the question is: will you be part of the revolution, or part of the statistic?
Ready to shield your platform with the security fraudsters fear?
Talk to our security experts. Discover what Corytech can do for your business.







 Payments
Payments
 Solutions
Solutions
 Industries
Industries
 Services
Services
 Resources
Resources





.png)






